Published: May 10, 2024 | Last Updated: December 11, 2025
Cloud Risk Management: How to Identify and Mitigate Risks

Table of Contents
Cloud environments can offer newfound connectivity and innovation to businesses, but they can also create new doors for vulnerabilities. Understanding your risks in the cloud, and working to reduce their impact, is a vital part of maintaining a strong security posture as an organization. One way to approach this is by creating and implementing a cloud risk management strategy.
We’ll cover what’s included in cloud risk management, common security risks, and what to do to keep vulnerabilities low over time.
What is Cloud Risk Management?
Cloud risk management is a process used to find, evaluate, and reduce the risks of using cloud computing services. Businesses take a proactive approach with risk management to protect their applications, data, and infrastructure from potential threats.
The Importance of Cloud Risk Management
With cloud risk management, organizations can improve their business continuity, reduce the risk of data breaches, save money, enhance their compliance measures, and ensure their reputation stays intact. The difference between implementing cloud risk management and not can be the difference between the continuation or the end of your business.
Potential Consequences of Inadequate Risk Management
Failing to manage risks to cloud security can result in several different consequences, including:
- Data breaches: Data breaches can be incredibly damaging to your business. They cost organizations, on average, $4.45 million. Plus, 82% of breaches included data stored in the cloud.
- Financial losses: Financial losses tied up in the cost of a data breach include lost business, labor costs associated with identifying and mitigating the breach, regulatory fines, legal costs, and more.
- Compliance issues: Some industries are required to abide by certain data privacy regulations. If your organization has inadequate measures in place, you may face regulatory consequences.
- Reputational damage: While cloud risk management can improve your reputation, failing to account for potential risks can result in a damaged reputation and a loss of trust. Some customers may never come back.
Common Cloud Security Risks
Cloud risk management starts with identifying common cloud security risks. Understanding what could cause a problem for your business will help you shape a risk management strategy that will best protect your data and infrastructure.
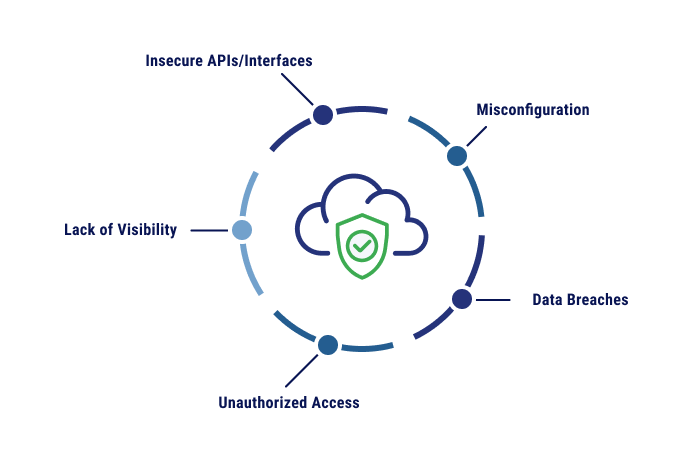
Misconfiguration
Cloud security settings are foundational to your cloud environment and can also be a significant culprit for data breaches. Small misconfigurations can leave large vulnerabilities, such as exposed sensitive data or easier entry points for unauthorized access.
Data Breaches
Cloud environments are attractive to cybercriminals because of how much data can be stored there. If you don’t understand what your security responsibilities are in relation to your cloud provider (more on the shared responsibility model below), you may be leaving your data open to infiltration.
Unauthorized Access
The two most prevalent attack vectors in 2023 included phishing and stolen or compromised credentials. When hackers gain access to credentials, they can quickly work their way into other systems and may even lock the rest of your organization out of part or all of your data and applications with a ransomware attack.
Insecure APIs/Interfaces
Cloud applications rely on application programming interfaces (APIs) to operate. However, if an API is not adequately secured, it can result in vulnerabilities that bad actors can use to reach sensitive data or impact the functionality of your systems.
Lack of Visibility
It can be hard to understand your security risks if you can’t see your entire cloud environment. Without the right tools and processes in place, businesses may not be able to effectively monitor their cloud environments and identify suspicious activity.
How to Assess and Mitigate Cloud Risks
After identification comes risk assessment and mitigation. By building the right models and using the right tools, your business can reduce security risks in the cloud.
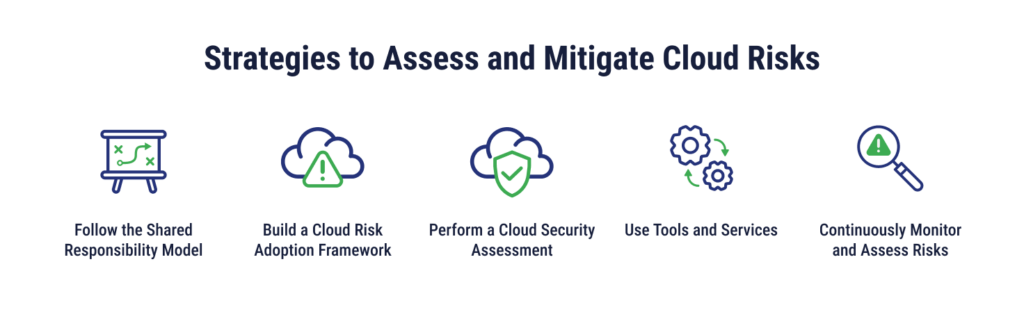
Study the Shared Responsibility Model
With a shared responsibility model, the cloud service provider shares some of the responsibility for cloud security, while the user is responsible for the rest. The level of responsibility will depend on the type of delivery model – IaaS, PaaS, or SaaS. For example, AWS may be responsible for the safety of their global infrastructure and the software running on it (compute, storage, data, and networking), but customers are responsible for the security of their operating systems, firewall, and customer data, among other things.
Build a Cloud Risk Management Framework
Once you have an understanding of your responsibility in the cloud, you can start to build a cloud risk management framework. This will include identification of risks, measuring the impact of these risks (or prioritizing based on what’s associated with more critical or sensitive data), planning risk mitigation strategies, creating reports, and implementing risk governance to ensure that plans are followed as described in the framework.
Perform a Cloud Security Assessment to Identify Risks
Based on what you’ve developed in your framework, perform a cloud security assessment to ensure that access controls, data security, and compliance measures are set up properly. You may want to leverage tools and conduct penetration testing – a simulation of an attack – to confirm that your risk management plans will work as planned.
Leverage Tools and Services to Mitigate Risks
The risks your business is likely to encounter will also dictate the security tools and services that will be more appropriate. Security tools you may want to incorporate will have features like encryption, security monitoring, and access control. Some are native to cloud providers, whereas others may be third-party solutions.
Firewalls and Intrusion Detection/Prevention Tools
- AWS: AWS WAF and Shield for web applications
- Azure: Azure Firewall and Azure Sentinel
Logging and Monitoring for Security-Related Events
- AWS: CloudWatch
- Azure: Azure Monitor and Azure Security Center
Integration with SIEM Tools
- AWS: CloudWatch can be integrated with third-party SIEMS, like Splunk
- Azure: Azure Sentinel supports third-party integrations and has built-in SIEM capabilities
Incident Response and Real-Time Threat Detection
- AWS: GuardDuty
- Azure: Azure Advanced Threat Protection
Continuously Monitor and Assess Risks
Risk management is never a one-time fix. The threat landscape is always growing and changing. To protect your cloud environment, you will need to constantly monitor for new vulnerabilities and threats. Create planned intervals for security assessments and dedicate resources to ongoing monitoring so that your cloud environment isn’t just secure in the present – it will be safer from threats in the future.
Taking a Proactive and Comprehensive Approach to Cloud Risk Management
Is it time to move from defense to offense? Do you need support for your security team? TierPoint can help you take a proactive approach to cloud risk management. Our experts can provide you with a comprehensive approach that leaves no stone unturned. Learn more about our IT security consulting services and get on the road to risk management today. In the meantime, download our whitepaper to explore some of the key defenses you can deploy to protect against top cybersecurity threats.

Table of Contents
-
Cybersecurity
Dec 8, 2025 | by Ed Mahoney
How AI Threat Detection Is Transforming Cybersecurity
VIEW MORE -
Cybersecurity
Nov 26, 2025 | by Matt Pacheco
EDR vs MDR vs XDR: Key Differences Explained
VIEW MORE -
Cybersecurity
Nov 17, 2025 | by Matt Pacheco
Cloud Infrastructure Security: Key Threats & Best Practices
VIEW MORE
