June 19, 2024 | Matt Pacheco
Top Cloud Data Protection Best Practices to Overcome Challenges

Cloud computing opens up new possibilities for scalability, integration, and product development, but it also provides another attack vector for cybercriminals. Businesses face many challenges when it comes to safeguarding their data, but there are steps you can take to overcome these obstacles and ensure cloud data protection.
What is Cloud Data Protection?
Cloud data protection includes measures businesses take to safeguard their information stored in the cloud. With 70% of organizations having half or more of their infrastructure in the cloud and 65% of organizations using multicloud environments, organizational reliance on the cloud means that data integrity and security are vital.
Different cloud data protection projects can involve cloud data security measures, data backup and recovery, data visibility, and governance and compliance measures around data protection and privacy.
Why Cloud Data Protection Matters
Due to the growth of cloud adoption across businesses, vast amounts of data are being stored and processed in the cloud, and threats associated with this data are also growing simultaneously. Even businesses that rely on cloud services need to be mindful of the shared responsibility model – managed public cloud providers are responsible for infrastructure-level security, but customers are responsible for the security of other parts of their systems, including applications, sensitive data, and operating systems.
Key Challenges in Cloud Data Protection
Even when business owners are aware that cloud data protection should be a priority, the complexity and volume of work needed to improve the security of cloud data can feel challenging.
Data Backup and Recovery
Data backup and recovery ensures that data is recoverable when a disruption or outage occurs. When businesses don’t have backup and recovery measures in place, it can lead to costly consequences. The average cost of a data breach in 2023 was $4.45 million. 82% of these breaches happened with data stored in cloud environments. This is why understanding your part in the shared responsibility model is crucial.
Data Visibility and Control
You can’t control what you can’t see. Maintaining visibility on where data lives in your system, as well as how it’s being used and who has access to it, is an important first step in determining how best to protect the data. Organizations often struggle to gain full visibility over their cloud environments, or they don’t have the right tools and processes in place to monitor activity and manage access controls.
Compliance with Regulatory Standards
Certain industries have stringent regulatory requirements for data privacy and security. Oftentimes, cyber insurance policies require that companies meet specific data protection standards. Failing to stay compliant can mean businesses are subject to fines and other legal consequences.
Misconfiguration and Human Error
Even when organizations take on data protection projects, flaws in configuration or manual mistakes can create vulnerabilities that make it easier for cybercriminals to infiltrate. Without the right team in place and regular standards checks, businesses can feel secure but still be prone to cyberattacks.
Data Residency and Sovereignty
What you need to do to achieve compliance with data protection will depend largely on your data residency and sovereignty. Data residency is concerned with the physical location of data storage, whereas data sovereignty is more about the regulations and laws around the governance of your data based on that location. If you have data in multiple locations, this can make your compliance requirements more complex, quickly.
Changing Threat Landscape
Cybercriminals develop new attack tactics constantly. Artificial intelligence is making it easier for bad actors to fake voices, write more effective spearphishing emails, and develop more sophisticated social engineering attacks. Organizations need to be informed about the latest threats and what they need to do to keep their security measures relevant.
Cloud Data Protection Best Practices
Face your business challenges and improve your security posture by applying these nine best practices for cloud data protection and cloud data privacy.
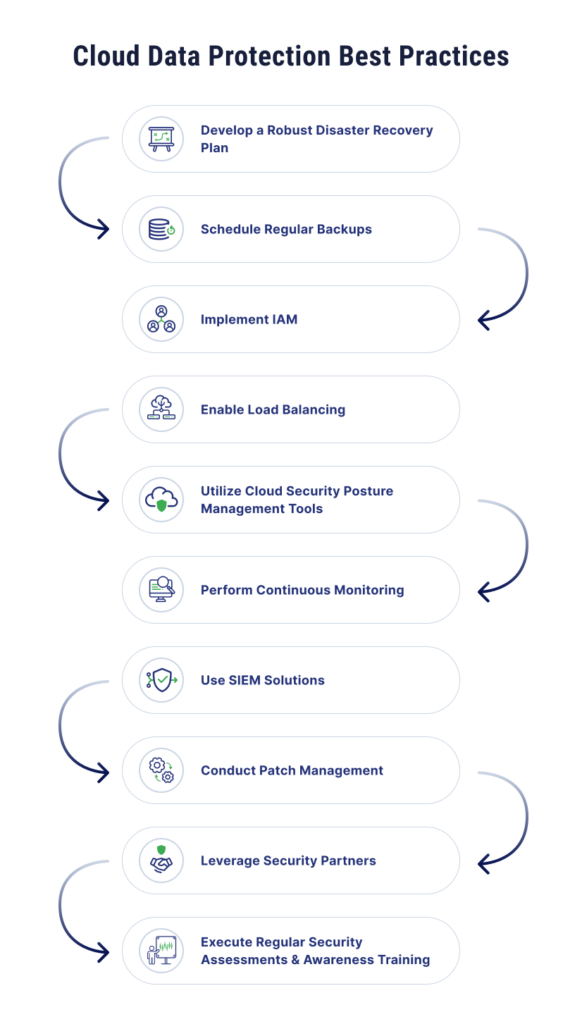
Develop a Robust Disaster Recovery Plan
A well-defined disaster recovery plan will include any and all steps your organization needs to take to protect your data and applications in the event of disruptions. It should outline who is responsible for what, which teams and individuals need to be informed of the incident, what should be switched over automatically or manually, and what needs to be done to restore “business as usual” at the organization. To ensure the plan is effective, it’s important to test it annually, at a minimum.
Schedule Regular Backups
The schedule for regular backups should be determined based on how much data your business can lose in an outage or breach without causing a significant impact on your business processes. A recovery point objective (RPO) may be 5 minutes, 5 hours, or even 5 days. What your business can tolerate will depend on your industry and may vary based on the types of data you are looking to protect.
Implement IAM
Identity and Access Management (IAM) can help you define user roles and permissions in the cloud. It can also create a framework for multi-factor authentication. Developing IAM allows businesses to better control access to cloud resources based on user type.
Utilize Cloud Security Posture Management Tools
Your security posture isn’t fixed in time. It needs to be maintained through management solutions. Cloud security posture management (CSPM) can scan a cloud environment for security misconfigurations, empowering businesses to address vulnerabilities proactively.
Perform Continuous Monitoring
Monitoring can be made easier through artificial intelligence (AI)-powered tools, which can pick up on suspicious behavior based on pattern recognition. Anomalies that may fly under the radar can be more quickly spotted with AI, and continuous monitoring with AI tools offers a more cost-effective way to keep tabs on your cloud environment.
Use SIEM Solutions
Security Information and Event Management (SIEM) solutions take security data from different sources in a cloud environment and aggregate them into one view, making it simpler for security teams to see and respond to incoming threats.
Conduct Patch Management
When vendors find vulnerabilities, they create patches to address them. Businesses should regularly update their software and firmware in the cloud to mitigate issues from these known vulnerabilities, shortening or eliminating the possible window available to attackers.
Leverage Security Partners
Staying up-to-date on the latest cloud security trends is a full-time responsibility and can be difficult for small IT teams to accomplish effectively. By leveraging cloud security partners, IT leaders can add expertise to their team and gain access to advanced security solutions that may be out-of-reach for smaller organizations.
Execute Regular Security Assessments and Awareness Training
Just like monitoring and management should be constantly on your to-dos, regular security assessments and organizational training should never fall off your list. With scheduled security assessments, you can identify weaknesses and address them before they become bigger problems. Security awareness training can add a line of defense to your organization, arming your employees with more cybersecurity knowledge to stop potential threats.
Ready to Take Cloud Data Protection to the Next Level?
TierPoint’s IT Security Consulting services can help you bring your cloud data protection to new heights. We can augment your existing team with our experienced cloud security consulting experts. To learn more about boosting your security posture and developing defenses against top cloud security threats, read our whitepaper.

